My Kingdom for a Flag!

- foxtrotzulu94
- Feb. 13, 2018
An MJOLNIR and Hayabusa Spartan capture the Blue team's flag in a match on the map "High Ground"
(Halo 3 - Copyright 2007 Microsoft Studios, Bungie, 343 Industries - Source)
There was nothing quite like playing a match of Capture The Flag (CTF) in Halo on Xbox Live back in the day. Bring a couple of friends over, break out all the bags of chips and soda you've been stacking up and just play non-stop until the late night hours. Maybe I'm just a huge nerd, but it was a great way to spend a Saturday night. I haven't quite stopped being a nerd, but I now find myself partaking in a slightly different kind of CTF game.
The kind of CTF I'm doing nowadays usually has you to sifting through memory dumps, raw hex and x86 assembly code to find the secret hidden in an average looking file. It's where you get to build things to break other things that people once thought were secure (all of this, in a safe, legal, controlled environment, of course). These CTFs I'm talking about are information security competitions that require you to find messages (flags) embedded in regular looking data or locked away behind some layers of security. However, they are as much of a competition as they are a learning experience in real-world cybersecurity challenges for anyone who doesn't know otherwise. And when I started out, I knew nothing.
First Time for Everything
During my undergrad in Montreal, it was uncommon to hear about people doing CTFs, whether online or in-person. Most often, you'd hear about the dozens of hackathons being hosted by different universities every weekend and publicized for all students through the Major League Hacking website. However, hackathons aren't about "hacking" in the popular definition (what most people think of as hacking is actually cracking). So they're not at all related to CTFs and other info-sec competitions.
What ended up bringing me into the world of CTFs, security and pwning was The Computer Science Games. While not strictly a CTF competition, they have a number of challenges that were heavily related to information security. One such challenge that is open to all participants over the weekend is "Puzzle Hero": a jeopardy-style, flag finding collection of puzzles, released periodically throughout the three days of competition. Puzzle Hero was not centered around cybersecurity, reverse engineering or cryptography, but it had all these categories as puzzles.

The ETS Main Hall on Day 1 of the 2014 edition of CS Games. Teams are seen here starting Puzzle Hero, preparing for the Scavenger Hunt (a non-technical challenge) and also finishing up Dinner. Above, in-center is part of Concordia University's team in White and Maroon shirts.
(Picture by Lambert Le - lambertle.ca)
My first CS Games was in 2014 at l'École de Technologie Supérieure in Montreal. With the minimal amount of C++ I had learned in my first year of Engineering and a lot of googling throughout the weekend, I remember being able to solve some of the puzzles. But there were clearly others beyond my reach. Cracking a weak AES cypher and leveraging the vulnerabilities of a linear PRNG were among the things I remember not even knowing where to start. But some of my teammates knew how to solve them. So I learned from them, I slowly understood and, after the competition, I began to dive deep into low-level programming.
That summer, I played around with cross-compilers, linkers and got really good at reading hex dumps. Following an online cookbook, I built a custom version of Linux from source code and became intimately acquainted with dynamic vs. static linking and all the operating system and compiler security features, like GNU RELRO. The more I looked online, the more I seemed to find and the more I realized how little I knew about all this, and how it was never even given a passing mention in any of my lectures. Particularly important to understanding all of this and to drive the point home was the one famous article: "Smashing the Stack for Fun and Profit" by Aleph One. Needless to say, I was hooked from that moment on.
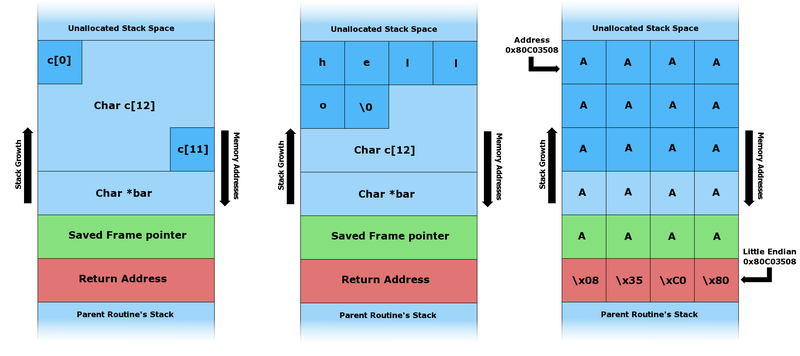
The image shows a common vulnerability in C programs known as a Stack Buffer Overflow. An exploit that takes advantage of this vulnerability effectively "smashes" the stack to overwrite the return address of the calling function.
(Image is Public Domain)
CS Games remained a constant throughout my four years of undergrad at Concordia University. My teammates and I would practice and improve over time, and each year we inched closer to winning 1st place in that competition. While my time in SCS and CS Games is best left for another blog post, it's no doubt that that's what got me started in programming competitions and left me with some of the best memories of my time as a student. Which is why I was incredibly sad when my time came to an end after I graduated. But I could only stay away from it for so long...
Developers by Day, Pen Testers by Night
After graduating and starting my full time job, I didn't think I'd be going back to any kind of competition. But, I'd soon find out most of my team at work also had a competitive programming background, and some of them were as eager as I was to get back into it outside of work. One of my coworkers, Owais, and I checked which competitions we were still eligible for as professionals, and soon found out that CTFs were a perfect match. So in January we both saw that there was an online CTF coming up in the first week of February: the qualifiers for Codegate CTF 2018 in Seoul, South Korea.
We recruited two of our co-workers, Vishnu and Yijing, and signed up for the 24 hour long competition. We were not expecting much since Owais and I were quite rusty in our competitive programming skills (having a steady job makes you lazy at the end of the day), and it was a first for Vishnu and Yijing. The competition started on Saturday at midnight hour UTC, which translated to Friday at 4PM for us. The whole team went to Owais' and Vishnu's place at around that time and started coding. In the end, we solved 4 of about 18 challenges that were posted over the course of the competition and fared Ok considering the sheer amount of people that were participating online. It wasn't enough to pass the qualifying round, but we were happy for it being our first time together.

Among cans of Coke and Pepsi Max, Laptops with terminal prompts and a Synthwave mix playing in the background our team, "!MS", was well past the 8th hour of the Codegate CTF 2018 Qualifiers. Team Members: Yijing (right), Vishnutheja (center), Owais (behind the camera) and myself (left)
(Picture by Owais Khan)
However, there were two important things about the whole experience:
- We found out we had a lot to catch up on: Within the hour the first three challenges of the CTF were posted, there had been at least 5 teams that had already solved them. We solved two of those over the course of the following 13 hours. As we later saw in some of the published writeups, there were tools that automated a large part of the work that we were doing manually. You often see simpler variation of these problems as real-world examples, but the solution is often a simple script put together to demonstrate the exploit. We were unaware of some of the more advanced tools like the python "pwntools" and "angr" packages that make certain common exploits and reverse engineering tasks incredibly straightforward. Likewise, there were concepts in cryptography we hadn't seen or practiced extensively enough to craft an exploit, but which we only found out afterwards by reading the writeups.
- It wasn't Halo, but it was still pretty fun: I know few people that can disassemble a binary and calculate the address in the Global Offset Table of that one function in glibc you need to make a Return-Oriented Programming exploit work. But I know even fewer people who enjoy doing that on a Friday night (and late into Saturday morning). While it's not what most people define as fun, it certainly was for our team. I had a blast getting together with them and working through the exploits. Tired as I was the next day, I'd do it all over again. Hopefully, we'll get good enough to make it past the qualifying round by next year.
Capture The Flag for Fun and Profit
To this day, there are still exploits and challenges beyond my reach. If anything, my team's Codegate CTF Qualifying round further cemented that fact and also gave me a much needed reminder that you lose the skills you don't use often. But to get better at anything you need to know exactly what it is that needs to improve and how to get there. For CTFs, sometimes it's a matter of learning the concepts or just making sense of how they craft the exploit based around it. It's equal parts technical knowledge and creative problem solving: think about something outside of the box and you might just find that's all you needed to break the box.
PyJail /__\ ____________| | |_|_|_|_|_|_| | |_|_|_|_|_|_|__| A@\|_|_|_|_|_|/@@Aa aaA@@@@@@@@@@@@@@@@@@@aaaA A@@@@@@@@@@@@@@@@@@@@@@@@@@A ^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^ [!] Rule 1. After 3 day, the Light will be Turned Off then you Cannot see anything. 2. Cannot Use Some Special Characters in PyJail. 3. For 10 days, You can enter 38 characters per day. Can You Escape from Here ?? Name : [day-1] ################## Work List ################## coworker : Find Coworker For Escape tool : Find Any Tool dig : Go Deep~ bomb : make boooooooomb!!! ############################################### javier : [Dig] depth = 1 [day-2] ################## Work List ################## coworker : Find Coworker For Escape tool : Find Any Tool dig : Go Deep~ bomb : make boooooooomb!!! ############################################### Traceback (most recent call last): File "./Impel_Down.py", line 140, in <module> result = eval("your."+work+"()") File "<string>", line 2 () ^
One of the challenges of Codegate CTF 2018 Qualifiers was "Impel Down". The source file of the program was not provided, but by manipulating the input with certain control characters and causing an error, Python would reveal a notorious eval statement which ultimately serves as the basis of the exploit in this challenge.
So, whether you're a computer science student or a professional software developer in the industry, I cannot recommend enough doing a CTF at least once in your life. You might find it's not for you and call me crazy or masochistic for liking them. But, you might also discover an entire field of computers that you could be unaware of now and get to know it better.
I'd say CTFs are especially useful for anyone coming from a competitive programming background, since unlike ACM ICPC and what you might find on Hackerrank or similar platforms, a lot of the vulnerabilities put into CTF challenges have been seen in the wild in some shape or form over the past 20 years. And it's unlikely to be any different in the future. So, might as well get acquainted with them in an environment that actually allows you to test out creative ways of breaking into systems (legally). It can only make you a better software developer.
Remember, you don't know what you don't know ;)